vRealize Operations Tenant App for Cloud Director (TA) is a great addition to any service providers Cloud Director deployment. Adding Tenant App allows end users to perform performance and reporting tasks without having to contact the service desk which reduces the amount of tickets in the queues and allows for the engineers to be doing more interesting tasks. In the install documentation it guides you through the process of adding users into the TA admin portal Administration > Access Management > Manage Users, in turn this will add users into vRops which can be seen here Administration > Access > Access Control > User Accounts. This approach is great but when you want users to be granted access in a more automated fashion we can use AD integration and the power of AD groups + vRops roles.
The below approach is focused around a service provider using a root domain for all LDAP logins e.g. each tenant is provided user logins for VCD which is fully under the control of the service provider and can be a secure internal domain.
for the below example we will be using the corp.local domain and a tenant Cyberdyne Systems.
High Level Steps:
1. Configure LDAP for VCD System and Tenant
2. Create AD users/ Groups
3. Import User/Groups into Tenant access in VCD
4. Configure vRops LDAP
5. Import AD access group and assign customer role
6. Enable tenant in TA
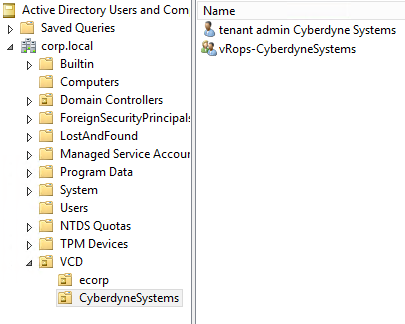
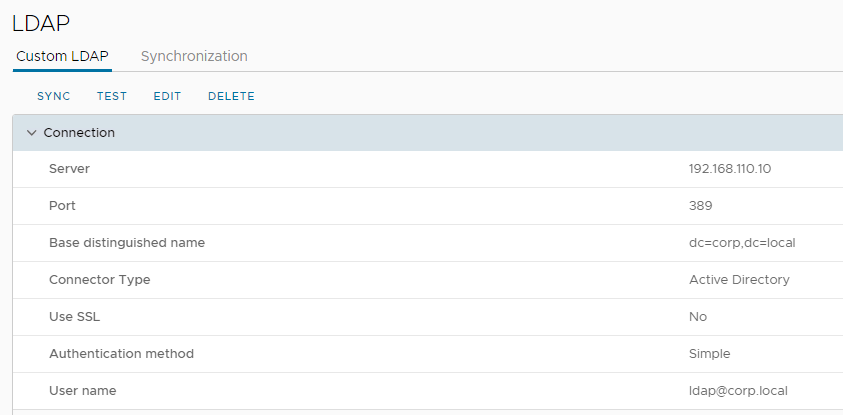
VCD System – LDAP config – This is configured a the root of the AD tree.
Org – Cyberdyne Systems – LDAP Config – points to a OU in the AD tree.
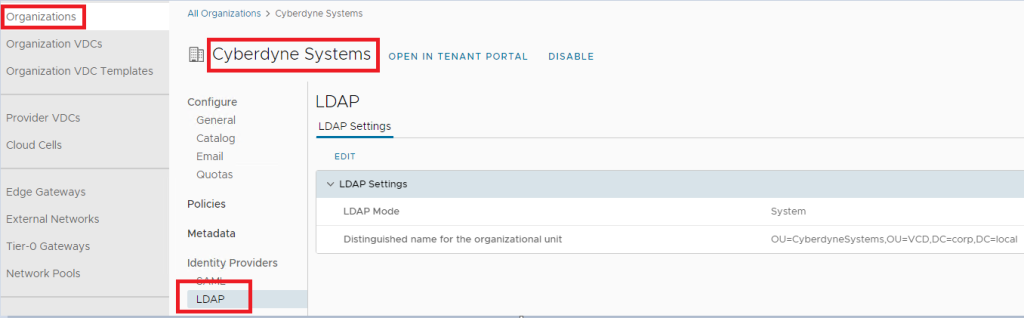
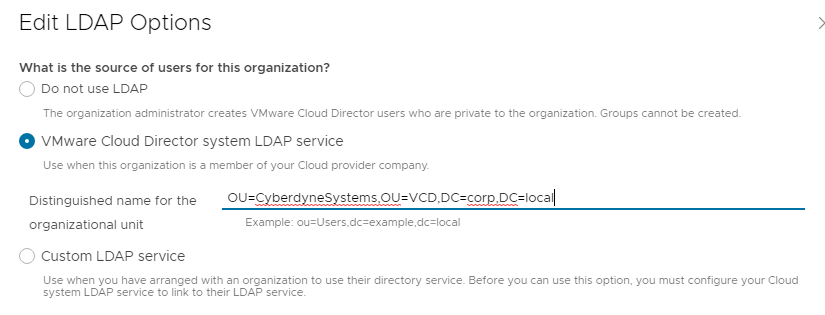
This allows for users to login to VCD using the corp.local domain account provided by the service provider.
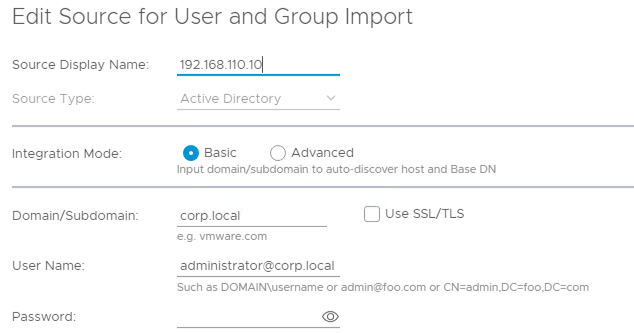
vRops
vRops will also require a LDAP connection to the same Active Directory so user and groups can be imported from the target OU’s, this is a shared platform and lab for me so I have it configured at this level DC=corp,DC=local, this is configured in vRops Administration > Access > Authentication Sources > Add
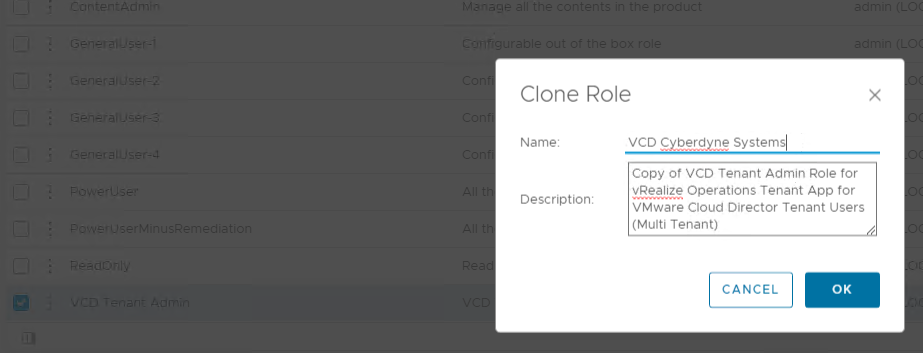
We now need to create a custom role for the tenant, when TA is installed and connected to vRops a default role is created named VCD Tenant Admin, we can use this as a template to get us started and tweak the permissions.
Clone the VCD Tenant Admin Role and give it a new name.
Now in AD create the users that will be used to login to VCD, also create a vRopsTA access group and add those users in.
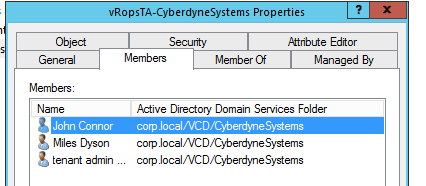
Import this into vRops – Sync the auth Source to make sure that it’s been updated, then go to User Groups tab and click the 3 dots next to the Add button and Import, search for the AD group name
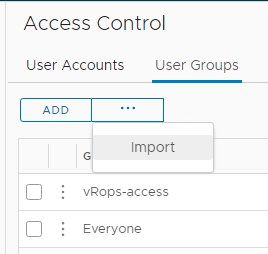
Search for the AD group name and select it, click next
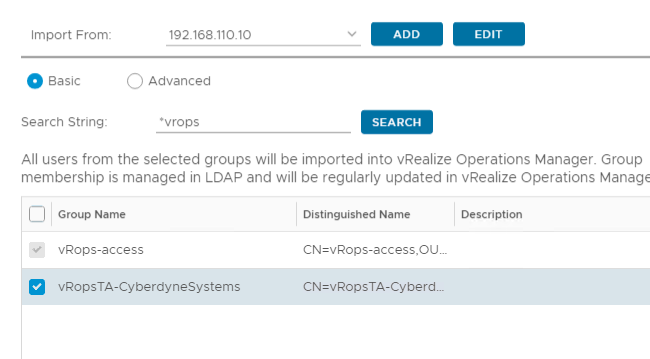
Drop down on the role select and find the role we created before, select it and click assign this role to the group, in the select Object Hierarchies find vCloud Tenant and in the Object side select the tenant and the Propagation tick boxes.

Note when you have imported the group you will now see the users in the User Account tab.
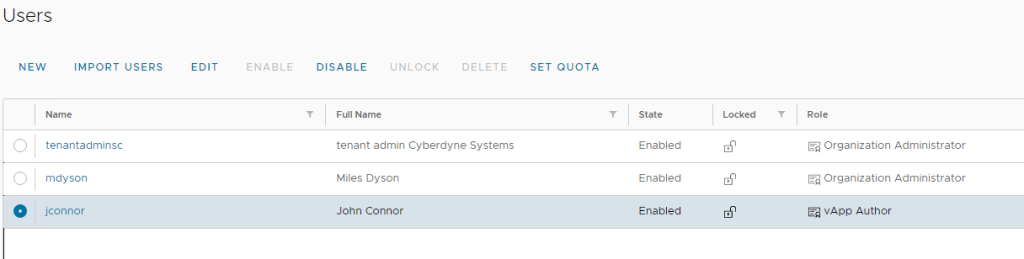
If not already done import the users into VCD under the tenant Administration > Users > Import … search and assign the VCD role for that user.
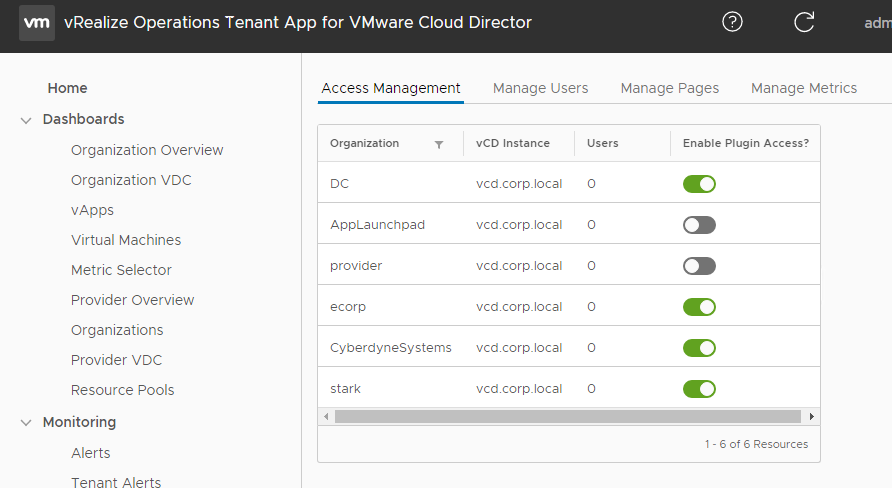
Login to the admin portal for Tenant App and make sure that the tenant is enabled under Administration > Access Management
Login to the tenant and the users and launch the Operations Manager plugin under More
If the VCD and vRops have both been setup to use the same attribute for the user name e.g. SamAccount or UPN then this should be a single sign on motion, if asked for login details this could be set differently or the custom role is incorrect. Note if you are having problems make sure to close the browser as it does keep session.